Utilities are under cyber threat, so what they can do about it?
Hey! Looks like you have stumbled on the section of our website where we have archived articles from our old business model.
In 2019 the original founding team returned to run Next Investors, we changed our business model to only write about stocks we carefully research and are invested in for the long term.
The below articles were written under our previous business model. We have kept these articles online here for your reference.
Our new mission is to build a high performing ASX micro cap investment portfolio and share our research, analysis and investment strategy with our readers.
Click Here to View Latest Articles
Critical infrastructure networks are increasingly being targeted by cyber criminals. Utility providers, in particular, are more frequently having to deal with data breaches as hackers look to disrupt or even destroy supply of vital services.
Symantec has linked a hacking group called Leafminer to Iran. The group is known to be targeting electric utilities in the United States and has successfully breached several networks using common tools and tactics like phishing emails and so-called watering hole attacks — a strategy in which a hacker infects a legitimate website that its target frequently visits.
So serious is the threat that the U.S. Department of Homeland Security set up a new centre devoted to helping protect critical assets — from banks to electric companies to manufacturing plants.
It was an important move as U.S. utilities have been under attack for some time. In 2017, Russian hackers, who are still purported to be active, hacked into the U.S. electric grid.
As reported by GTM: Russian hackers broke into theoretically secure “air-gapped” utility networks by first accessing the networks of trusted utility vendors, which have special access to update software, run diagnostics and perform other services. DHS claims there were "hundreds of victims."
Homeland Security, chief of industrial-control-system analysis, Jonathan Homer said the attackers “got to the point where they could have thrown switches” and disrupted the grid.
That very scenario occurred in the U.K. and Ukraine last year through the WannaCry and Petya cyberattacks, which took down the U.K.’s National Health Service and Ukraine’s electricity networks respectively.
In Australia, the Australian Energy Market Operator ramped up the nation's electricity infrastructure cybersecurity to protect the country’s power network, supported by the Australian Cyber Security Centre in Canberra.
The centre was founded during Malcolm Turnbull’s term as Prime Minister. He said at the time“the number one priority for my government and indeed for every government is the safety and security of the nation. We must not and will not wait for a catastrophic cyber incident before we act to prevent future attacks.”
The former PM had been kicked out of office by his own Party when the Federal Parliament’s computer network was hacked.
It isn’t just hackers that are putting data at risk. Internal failings are also on the rise. Late last year, California utility Pacific Gas and Electric Company(PG&E) was fined US$ 2.7 millionafter it left sensitive information – including hashed passwords for administrators that attackers could have reverse-engineered – exposed to the internet.
Data breaches within the utility sector could prove catastrophic at some point, so how can companies mitigate this problem?
WhiteHawk, a leading cyber security solutions provider, recently released a whitepaper detailing how cybersecurity officials can identify and address a majority of critical risks in real time through access to affordable risk auditing, rating, alerting, and mitigation services sector-wide.
For the full report, click here. In the interim, we’ll summarise the key points.
The issue
The US has over 3,300 utilities which are increasingly coming under attack.
A global survey by management consultant Accenture showed that 49 percent of utility executives believe their country faces a moderate risk of electrical supply interruption from a cyberattack on distribution grids in the next five years. Only 57 percent of those executives thought they were well-prepared for such an attack.
The Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) officials announced —for the first time—that Russia had beentargeting the energy, electric, nuclear, commercial, water, aviation, and other criticalinfrastructures in the U.S. The multi-stage intrusion campaign affected domain controllers,file servers, and email servers.
According to WhiteHawk’s report, a successful sophisticated attack on the utility sector could cripple a range of critical services including:
- Hospitals
- First responders
- Banks
- Power plants
- Airports and air traffic control
- Traffic controls on thousands of miles of heavily travelled roads
Types of attack
Attacks are becoming more and more sophisticated. However, many small and mid-sized utility companies are under-prepared and particularly vulnerable. Staff shortages or lack of employee training on IT and OT connections, computer security, and active cyber threats increase risks for these companies.
So what should they be aware of? The types of attack include:
Malware:Malware is software designed to covertly operate on a compromised system without the knowledge of the user. Malware can encompass ransomware, spyware, and command and control software. Malware attacks are the best known types of attacks because of their potential to inflict severe damage across a utility architecture.
Spear phishing:Spear phishing uses carefully worded emails that sound authentic to the target. The attacker tries to induce the target to open or download an attachment containing malware.
Structured Query Language (SQL):SQL is a language designed to manipulate and manage information in a database. It is now regularly found in commercial and open-source databases. SQL injection, or SQLi, is a type of cyberattack that targets databases using specifically crafted SQL statements. The attack induces a system to execute unexpected or undesirable actions.
A successful attacker may be able to bypass authentication, infiltrate, steal, modify, corrupt, or delete information, and run an arbitrary code. The attacker may also gain root access to the entire IT business or operational system.
Denial-of-Service (DoS):DoS attacks focus on disrupting or preventing legitimate users from accessing websites, applications, devices, or other resources. Criminal organizations have used these attacks to extort money. Activist groups conduct them to further their agenda. And state actors use DoS attacks to retaliate against an enemy.
So, now that you know what to look for, how do you mitigate?
Mitigation solutions
WhiteHawk’s report references Accenture’s five-step approach to combating cyberattacks on the US utility sector:
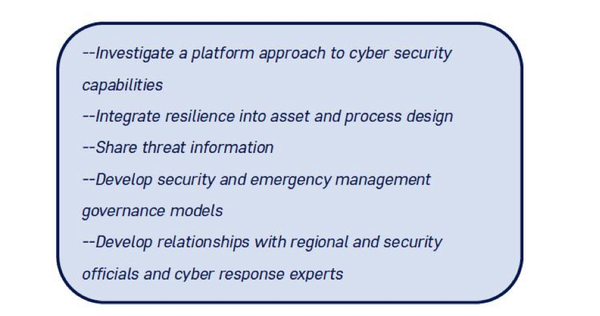
For this to work, WhiteHawk states “Congress would likely have to pass legislation in order for the U.S. to accept and enforce this approach or something similar nationwide. The law would have to include provisions for significant federal and state funding to train current personnel, attract and train new recruits, and ensure up-to-date technological support. For this effort to succeed across the country, utility units would need to reorganize to eliminate the cultural and organizational silos often present between operational and technical business units.”
That’s a big job and could be time restrictive and expensive.
In the meantime, WhiteHawk suggests the following:
- Optimize an annual cybersecurity online compliance based self-assessment or risk baseline.
- Implement affordable access to best of breed cyber risk ratings, continuous monitoring, risk indicator alerting and mitigation services sector wide.
- Maintain inventory of control system devices.
- Leverage the following recommended technologies:
- Implement Operational Technologies (OT) to improve unified monitoring and detection strategies to address threats;
- Use Industrial Control Systems (ICS) sensors, which provide an opportunity to improve unified monitoring and detection strategies to address threats;
- Implement technologies across OT and ICS that identify threat vectors and include the use of honey pots to attract and trap adversaries.
Some options are:
- Radiflow is a leading provider of cybersecurity for ICS and supervisory control and data acquisition (SCADA) networks in the utility sector.
- Sandbox Technologies is a software management strategy that isolates applications from critical systems and other programs. Using tools like VMWare or Docker, containers are made to create a disposable sandbox; Linux and Solaris have it built in. Other tools perform process isolation like Black Box (sandbox technology for ICS). Black Box offers a number of solutions for integrating SCADA systems with newer technologies and leveraging existing ones.
- D3 Security is a single incident management solution that enables situational awareness across cyber threats, risk assessments, and the status of compliance with standards such as North American Electric Reliability Corporation (NERC).
- CyberSponse CyOPs platform is an enterprise-built security orchestration and security automation workbench that empowers security operation teams. CyOPs provides teams with the means to work smarter and respond in near real time. The platform includes capabilities for triage and investigation of alerts and supports collaboration and remediation between team members.
- Mission Secure Inc. (MSI) provides an innovative approach and patented software/hardware platform to help power organizations stay ahead of the evolving cyber physical threat curve. Its Secure Sentinel Platform delivers a reliable means of assuring integrity within the operator’s specific system and the ability to take corrective action preventing potentially catastrophic consequences.
To ‘server’ and protect
Cyber attackers or hackers are lurkers, waiting patiently in the shadows before attacking unaware prey.
The ongoing challenge, however, is that companies can never fully be aware of when an attack might occur.
What they can do is protect their servers, be more vigilant when it comes to cyber protection, commit to frequent tech audits and work hard to identify threats.
General Information Only
This material has been prepared by StocksDigital. StocksDigital is an authorised representative (CAR 000433913) of 62 Consulting Pty Limited (ABN 88 664 809 303) (AFSL 548573).
This material is general advice only and is not an offer for the purchase or sale of any financial product or service. The material is not intended to provide you with personal financial or tax advice and does not take into account your personal objectives, financial situation or needs. Although we believe that the material is correct, no warranty of accuracy, reliability or completeness is given, except for liability under statute which cannot be excluded. Please note that past performance may not be indicative of future performance and that no guarantee of performance, the return of capital or a particular rate of return is given by 62C, StocksDigital, any of their related body corporates or any other person. To the maximum extent possible, 62C, StocksDigital, their related body corporates or any other person do not accept any liability for any statement in this material.
Conflicts of Interest Notice
S3 and its associated entities may hold investments in companies featured in its articles, including through being paid in the securities of the companies we provide commentary on. We disclose the securities held in relation to a particular company that we provide commentary on. Refer to our Disclosure Policy for information on our self-imposed trading blackouts, hold conditions and de-risking (sell conditions) which seek to mitigate against any potential conflicts of interest.
Publication Notice and Disclaimer
The information contained in this article is current as at the publication date. At the time of publishing, the information contained in this article is based on sources which are available in the public domain that we consider to be reliable, and our own analysis of those sources. The views of the author may not reflect the views of the AFSL holder. Any decision by you to purchase securities in the companies featured in this article should be done so after you have sought your own independent professional advice regarding this information and made your own inquiries as to the validity of any information in this article.
Any forward-looking statements contained in this article are not guarantees or predictions of future performance, and involve known and unknown risks, uncertainties and other factors, many of which are beyond our control, and which may cause actual results or performance of companies featured to differ materially from those expressed in the statements contained in this article. S3 cannot and does not give any assurance that the results or performance expressed or implied by any forward-looking statements contained in this article will actually occur and readers are cautioned not to put undue reliance on forward-looking statements.
This article may include references to our past investing performance. Past performance is not a reliable indicator of our future investing performance.

